Finally we have a interface for Administrative Units. I have been in private preview for a time now and test this interface with customers. There are always things I will see to be better but a very good start. If you hope that you can release PowerShell for now, then the answer is no. We still need it because we waiting for dynamic assignments of members. Until we have dynamic assignments we need to have a script running to add new users to AU.

Another thing with the interface is the confusing around assignment of administrative users. In the picture below we have Password administrators but they with the scope “Directory (Inherited)” is not member of the AU. Only the users with scope “This resource”. If an user have Directory (Inherited) then the admin user is assigned directly to the admin role in Azure AD and not limited to this scope. This is a bit confusing and not clear.

How can we start use Administrative Units?
1, Start to create a new Administrative Units.

2, Add users to the AU. Users is all members the admin role can see and change. You can choose to add user by user or bulk add members.
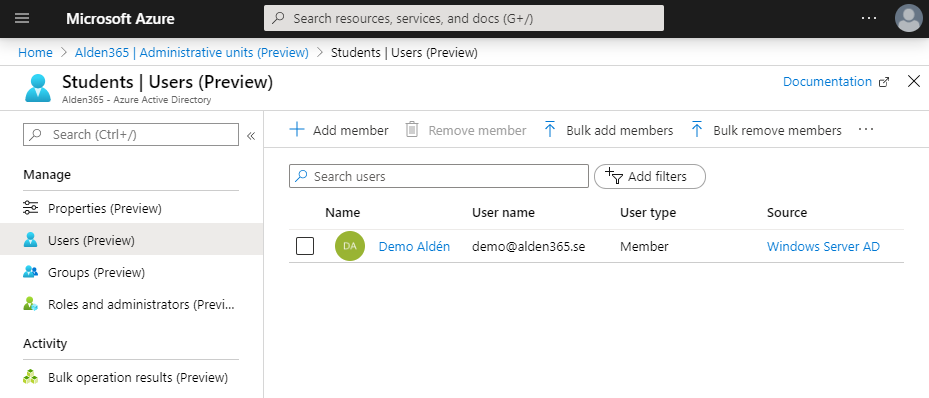
3, Groups is similar as users. If you need to administer groups then add them to the list.

4, After you assign users and groups then we need to add roles the AU. Today we have only six roles and there are some limitation also. Privileged Identity Management (PIM) is not supported but you can have PIM on all other roles that is not part of AU.

5, Add admin users to respective role for the scope of users and groups created earlier. Below we need the role to reset passwords.

6, Next step is to sign-in and reset password on members in AU. Sign-in to https://admin.microsoft.com give you only the users you can see.
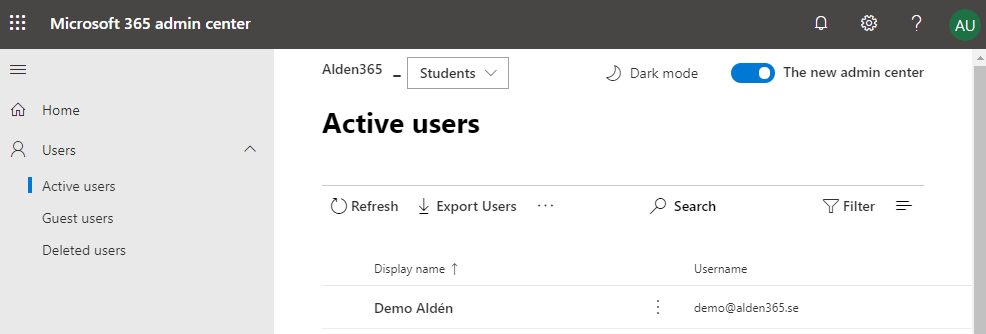
7, Sign-in to https://portal.azure.com and navigate to Azure Active Directory will display all users but you can only reset password on users limited to the AU. A way is to block Azure Management with Conditional Access to get around to the problem.
