Description
In this blog I will walk throw the basic configuration of creating an playbook that will isolate a machine that is onboarded to Defender for Endpoint. This operation can also be done from the Defender Security Portal without using Sentinel. To be able to complete this setup you will need to have Microsoft Defender for Endpoint + Microsoft Sentinel. The connectors should be enabled in Microsoft Sentinel is Microsoft 365 Defender.
In this example I will use the template for Entity trigger. This means that I can kick off the playbook and choose which machine I want to isolate.
You can also choose template with incident or alert trigger. This is a better option if you want to automatically trigger this for some kind of event.
Sentinel Configuration
Open you Sentinel instance and go to Automation->Playbook Templates->Isolate MDE Machine using entity trigger. You can rename it to a naming convention that is good for your organization and setup during the installation. This will configure an Logic App with the name you chosen in the step before.
Configure Permissions
First you will need to configure Microsoft Sentinel Responder for the Managed Identity. You can find this under the Logic App you just created:

Now go to Azure role assignments->Add role assignment and select the subscription or resource group where Sentinel is created. You will add the permission Microsoft Sentinel Responder. You will do this setting to give the Logic App permissions to make updates in Sentinel.
Now we also need to give the managed identity permissions to isolate the machine. To be able to do this we will give it Machine.Isolate permission. We will run a PowerShell script against Entra ID to configure this permission.
$MIGuid = 'Value find under picture above <Object (Principal) ID>'
$MI = Get-AzureADServicePrincipal -ObjectId $MIGuid
$PermissionName = 'Machine.Isolate'
$MDEServicePrincipal = Get-AzureADServicePrincipal -SearchString windowsdefenderatp
$AppRole = $MDEServicePrincipal.AppRoles | Where-Object {$_.Value -eq $PermissionName -and $_.AllowedMemberTypes -contains 'Application'}
New-AzureAdServiceAppRoleAssignment -ObjectId $MI.ObjectId `
-PrincipalId $MI.ObjectId `
-ResourceId $MDEServicePrincipal.ObjectId -Id $AppRole.IdIsolation
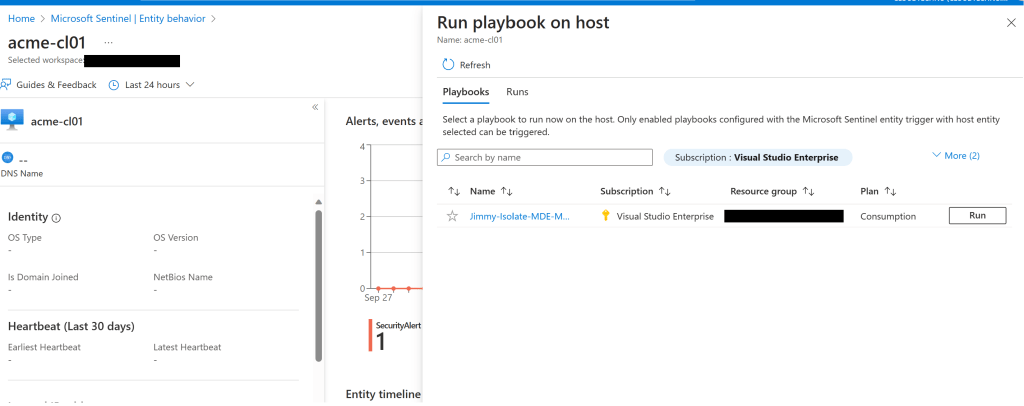
Now your playbook should show up as an alternative to run on the host entity. See image how to run:
Tips
If you place the Logic App in a different resource group which can be a good practice make sure that you give Sentinel access to this playbook resource group. This can be done under Microsoft Sentinel->Settings->Settings->Playbook permissions.
I also had issues to get the MDATPDeviceId to the playbook after I had configured Microsoft 365 Defender connector. What I needed to do was to go into the Microsoft Defender for Endpoint connector in Sentinel and select:

Summary
This is just an example how to setup a playbook with permissions. Good luck on your Sentinel journey!
Regards
Jimmy Lindö